How to Secure Your Small Business in the USA: A Beginner’s Cybersecurity Guide
Master cybersecurity for your U.S. small business! Learn simple steps to protect data, comply with laws, and save money. Start now!
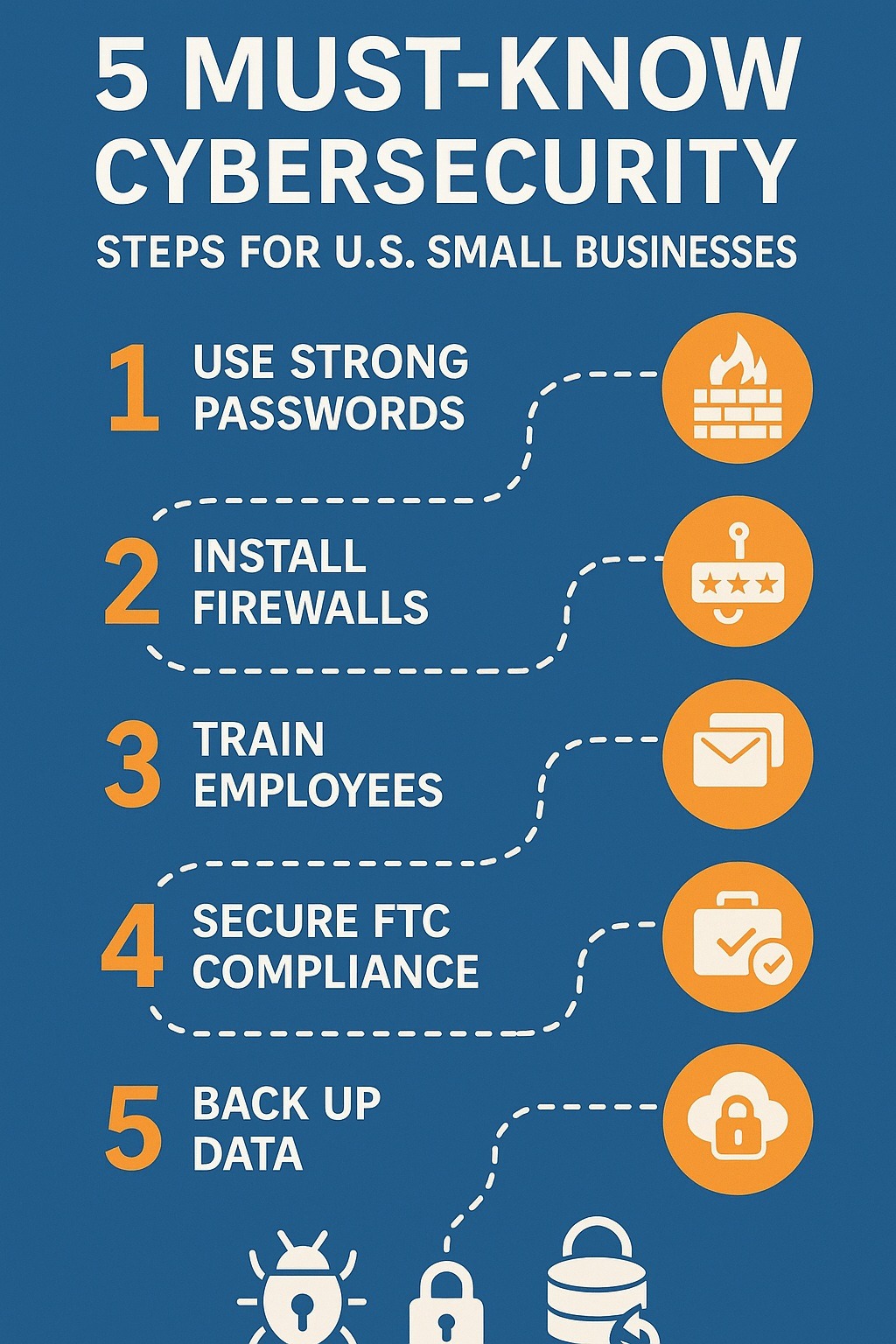
How to Secure Your Small Business in the USA: A Beginner’s Cybersecurity Guide
Master cybersecurity for your U.S. small business! Learn simple steps to protect data, comply with laws, and save money. Start now!


